
The value of an institution depends significantly on the way that critical communications,
transactions, and sensitive data is maintained. Stable regulation of access to information networks
is the cornerstone of the trust relationship necessary to conduct successful operations in the climate
of contemporary commerce, exchange, or management.
The fixed username and password schemes that proliferate across a vast majority of servers, websites,
and networks are largely ornamental and provide little to no defense against the highly advanced and
specialized tools wielded by modern cyber criminals, in addition to their susceptibility to being misplaced,
misused, lost, guessed, or stolen. One time password (OTP) technology is a proactive measure that institutions
can adopt to quell the danger of the threat posed through this inherent weakness.
OTP functions on the basis of a constantly regenerated numeric password sequence stored on a hardware token distributed
to end users; a unique password is created and subsequently entered to gain access at each log-in.
The hardware token is but a small part of the overarching procedure at work, what is of primary importance is the back
end authentication server. Feitian OATH Authentication Server (FOAS) is the man behind the curtain ensuring the smooth
functioning production and recognition of passwords stored on a user’s personal token. FOAS is engineered to comply
fastidiously with the stipulations set forth by the initiative for open authentication (OATH) consortium, a group which
unites the foremost industry experts and specialists in the field of strong authentication and determines standards of
easy integration and mutual interoperability of product offerings by participating members. As such FOAS can be used
seamlessly with any products certified to the OATH criteria making it a highly adaptable back end server solution.
When used in conjunction with components of the Feitian family of OTP products FOAS delivers a complete linear solution
which streamlines all authentication procedures from deployment to provisioning and maintenance; significantly reducing
IT overhead expenses. FOAS is a multi-channel identity verification system which can simultaneously validate the user to
a server and vice versa. Moreover, FOAS can establish a highly secure communication environment by providing digital
signatures for web based transactions.
FOAS is a centralized management interface that allows for the convenient centralization of different organizational systems.
One of the added benefits of the inclusive compliance architecture by Feitian is the ability of FOAS to support a wide range of
operating platforms, authentication protocols, programming languages, and web scripts. FOAS seamlessly integrates with existing
third-party authentication components as well as systems based on Radius protocol. Within the FOAS system administrators can easily
regulate functionality of all users, hardware tokens, agents and log requests. Basic functions such as adding, auditing, editing,
and deletion are supported through organized and intuitive profile grouping. Primary operators can assign and differentiate the
level of access rights and privileges for separate accounts as well as delegate responsibility by specifying distinctive management
roles for various accounts.
Within the FOAS system the process of token integration can be simple and intuitive. Typically there are three integration methods.
When feasible, one of the most convenient ways is to use the existing Radius protocol on the application server to install authentication
agents. Installation of OTP can also be done through the use of authentication agents which can save the time and energy it takes to
develop one’s own authentication agent. SDK interface integration offers the highest level of flexibility for the application
server with the ability to provide functions that are not covered in the previous two methods, however, it is not recommended
for all deployments.
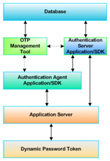
Essentially FOAS is comprised of three main components, they include: The authentication server, the management tool, and the authentication
agent. Supplementary parts are the OTP server database management system, the SDK interface for customization and the end user OTP hardware
tokens.
The authentication agent functions as a bridge between the authentication server and an application server. When an end-user logs in the
application server, an authentication request is sent and a result received from the authentication server through the agent in order to
decide whether the request is valid. The authentication agent is not necessary in every deployment scenario; applications integrated through
Radius have no need for an agent.
The management tool has an easy-to-use web interface to provide remote management and maintenance of end-users, OTP token, authentication servers,
authentication agents and log information from the database. The database management system is the foundation of the OTP Server Authentication
System containing most of the system data. Database management system can be chosen according to the specific demands of the client.
Benefits
FOAS is commonly acceptable across a wide range of platforms
FOAS can integrate smoothly into all major operating systems and support multiple databases with ODBC or other specific interface connection.
The FOAS system also maintains full set development interfaces in various programming languages.
System management is centralized and accessible
The web-interfaced management tool provides for secure remote management. Administrating the host of flexible settings is regulated
through central authentication for networks or computer operating systems. Support multiple authentication services with different
authentication settings on one computer.
Proven track record in the seamless execution of large scale highly diverse deployments.
FOAS handles loading balancing for multi-authentication services with up a concurrent service rate which can satisfy thousands
per second and concurrent support for up to ten million end-users. The system was engineered for co-operability with various authentication
agents.
OTP Server Authentication System largely enhanced the security of application servers
Dynamic passwords are randomly generated unique numeric sequences used as log-in credentials. Use of dynamic passwords can prevent
threats like replay, peep or monitoring. Fixed password can be used together with dynamic passwords to form two-factor authentication.
FOAS is fully available with the entire suite of Feitian OTP products including C300
With FOAS as a stable back end foundation users can adopt the Feitian hardware solution that best fulfills their specific demand.
OTP c300 token is improved by PIN protected access, both the challenge code and time-factor component are necessary to initiate a
challenge-response dynamic password or transaction signature. End-users can choose to cross validate an application server and vice versa,
preventing leakage of sensitive personal data.
OTP Server Authentication System V3.0 is an extraordinary complete value system
Intellectual property rights are self-owned so there is no need to worry about hidden costs. Localized development and production
lower transportation and customs expenses and provide timely after-sales service. Multi-lingual GUI design is provided standard.
Full provisioning of configuration and management tools is also standard. Advanced pre-sales and after-sales services are made fully
available at a nominal charge.
Design a custom tailored solution to satisfy unique circumstance and requirements
Choose which platform hosts and which database maintains application server. Both installation packages and the full set of API
interfaces are provided for efficient implementation. OTP Server Authentication System V3.0 is equipped with powerful management tools
to simplify end user oversight.
Features
1. Automatic Synchronization
The authentication server has the flexible feature to automatically synchronize a token during authentication if the token is found to be out-of-sync.
2. Multiple Token Supports
As for hardware tokens, OTP Server Authentication System V3.0 supports event-based OTP c100, time-based OTP c200, challenge-response OTP c300 and event-based-and-PKI-combined OTP c400 tokens.
OTP Server Authentication System V3.0 also supports mobile phone tokens based on event, time or challenge-response.
Again, OTP Server Authentication System V3.0 supports soft tokens based on event, time or challenge-response.
3. Multiple Authentication Methods
For systems that do not demand high security, it can be set to use single dynamic password to authenticate an end-user. Advantage of this method is that there is no necessity to remember another fixed password however security is quite low.
Dynamic passwords can be used together with fixed password to log in application servers that does not demand very high security. This method is commonly used to bring secure authentication of current application servers to the next level.
Challenge-response authentication method is normally used in application servers which demand high security and have end-users with advanced
technology knowledge. The disadvantage of this method is that authentication process involves many steps. However, it brings higher
interactivity and security to the application server.
Application servers sometimes use double-way authentication method against fake application server. End-users, before proving their personal
information, can verify the real application server.
For application servers which want to authentication critical transactions, transaction signature authentication method can be used. This is to make those critical transactions are indeed made by the end-user who claims to be.
4. RADIUS Server Support
According to pre-configured settings, the authentication server can send authentication request to a designated RADIUS server and collect
authentication result to send back to the application server
5. High Performance
The authentication server supports more than ten million concurrent end-users, and single server can reach concurrent processing rate
of 3000 times per second.
6. Multiple Algorithms
HOTP algorithm from OATH;
TOTP algorithm from OATH;
OCRA algorithm from OATH;
SM3 algorithm from National Security Standard
7. Prevention of Dictionary Attack
When the authentication server finds that a particular end-user has failed a certain times (can be pre-configured) of authentication,
it will lock that end-user. During locking, the authentication server will refuse authenticating this end-user until he/she has been unlocked. This is an effective prevention for dictionary attacks.
8. Prevention of Denial-of-Service Attack
The authentication server will delay sending a failed authentication result, which effectively prevents denial-of-service attacks.